How to secure S3 Bucket with KMS and test it
April 18th, 2022
Author: Ardi Hanitya
Cloud Senior Solution Architect | Westcon
|
|
|
|
|
|
Today we will cover AWS Key Management Service(KMS) with S3 bucket. Before we test it, we should know what KMS is.
AWS Key Management Service (KMS) gives you centralised control over the cryptographic keys to protect your data. The service is integrated with other AWS services making it easy to encrypt data you store in these services and control access to the keys that decrypt it. AWS KMS is also integrated with AWS CloudTrail, which allows you to audit who used which keys, on which resources, and when. AWS KMS enables developers to easily add encryption or digital signature functionality to their application code directly or using the AWS SDK. The AWS Encryption SDK supports AWS KMS as a root key provider for developers who need to encrypt/decrypt data locally within their applications.
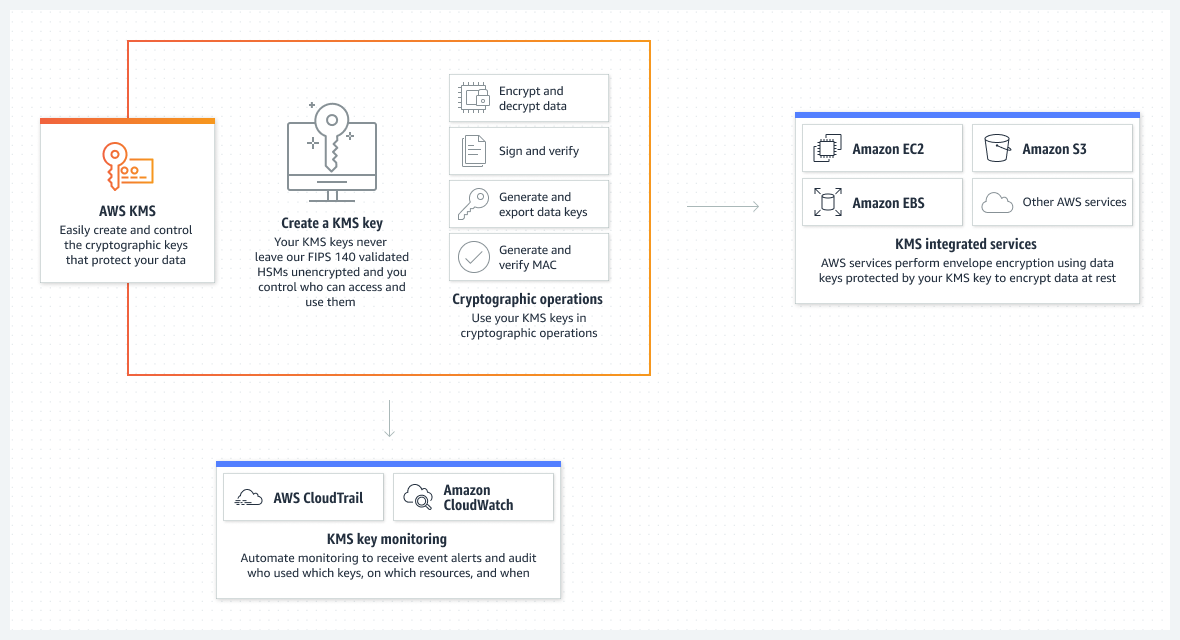
# Scenario
Create 2 IAM users (user-a and user-b), and attach S3 bucket and user-a with KMS. Test to upload some files to S3 bucket with user-a. Try to access and download the file with user-b, and try to open the file.
Ideally, a user with defined KMS can open the uploaded file. While other users do not, even though that user has AmazonS3FullAccess permissions. In this experiment, we will try to secure object files granularly.
Steps:
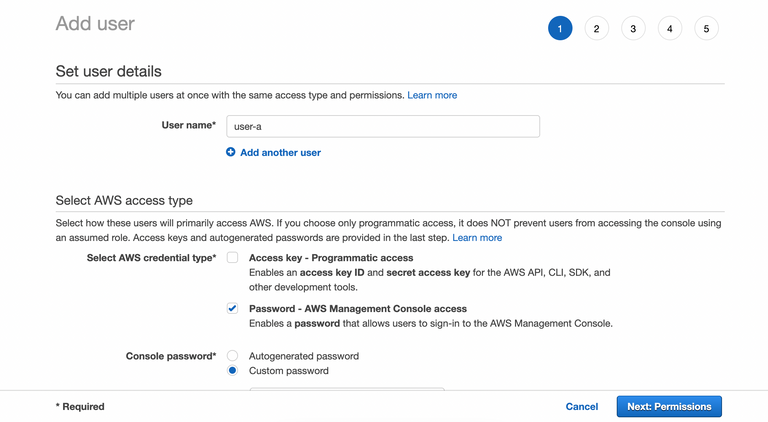
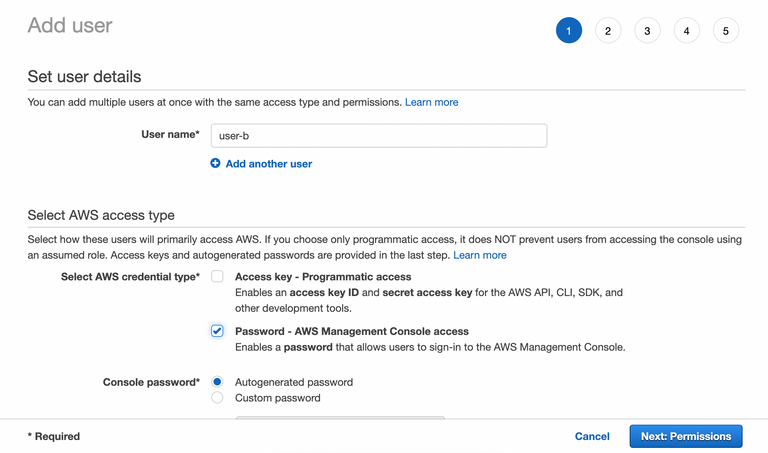
2. Give access to those users with AmazonS3FullAccess
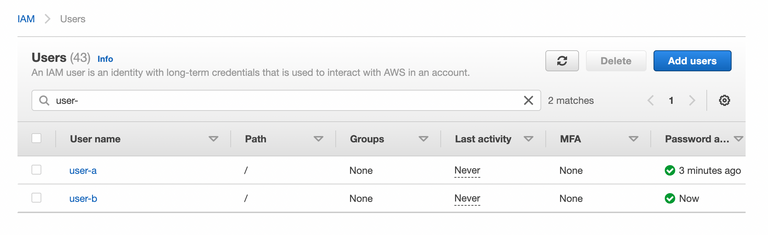
Please note: this is just an example to speed up the process. Giving full access is a bad idea in the real world. You can grant read-only access or restrict S3 bucket access to only get and put.
See how to restrict Amazon S3 here.
3. Create S3 bucket
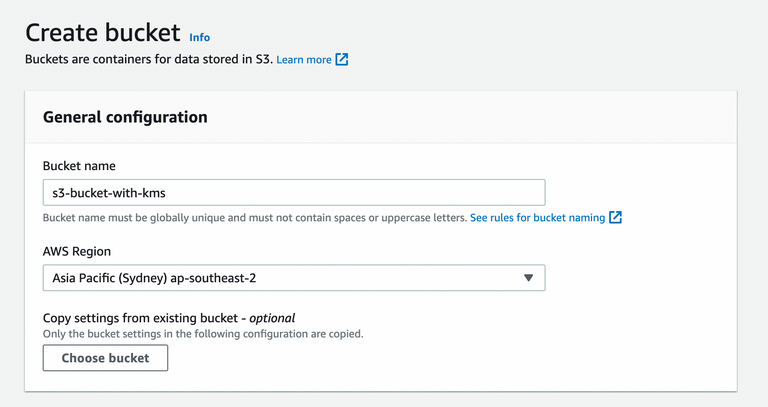
Make sure you don't give the public access to the S3 bucket because giving public access will reduce security. As much as possible, if you want to make the object public, you can create a pre-signed URL. Check the AWS S3 documentation for the pre-signed URL here.
4. Go to KMS, create and configure KMS key. Check the documentation for AWS KMS symmetric here
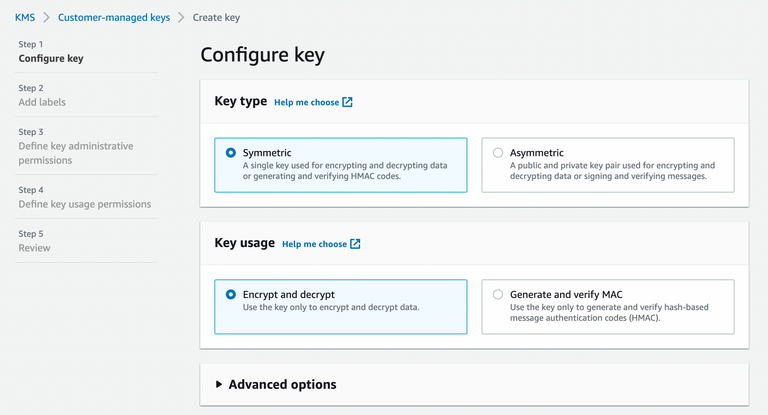
Choose Symmetric and Key usage: Encrypt and decrypt
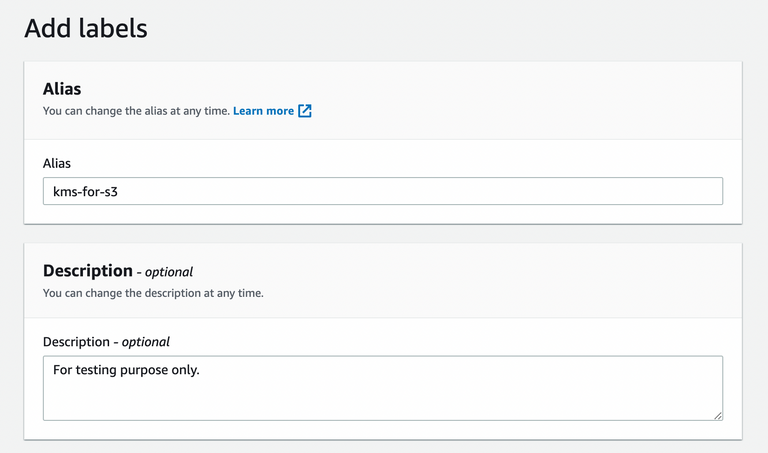
Add key alias.
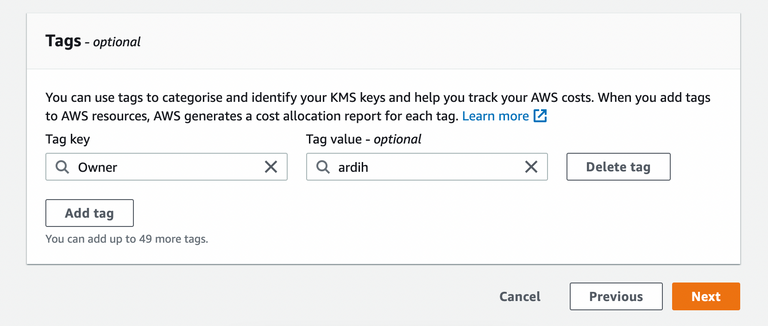
Add tags.
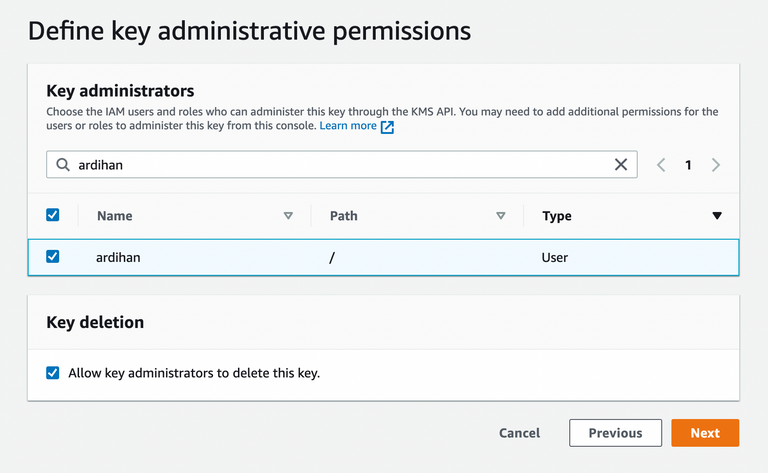
AWS documentation:
The default key policy created by the console allows you to choose IAM users and roles in the account and make them key administrators. This statement is called the key administrators' statement. Key administrators have permissions to manage the KMS key but do not have permissions to use the KMS key in cryptographic operations. You can add IAM users and roles to the list of key administrators when you create the KMS key in the default view or the policy view.
I use my own IAM user for Key Administrator.
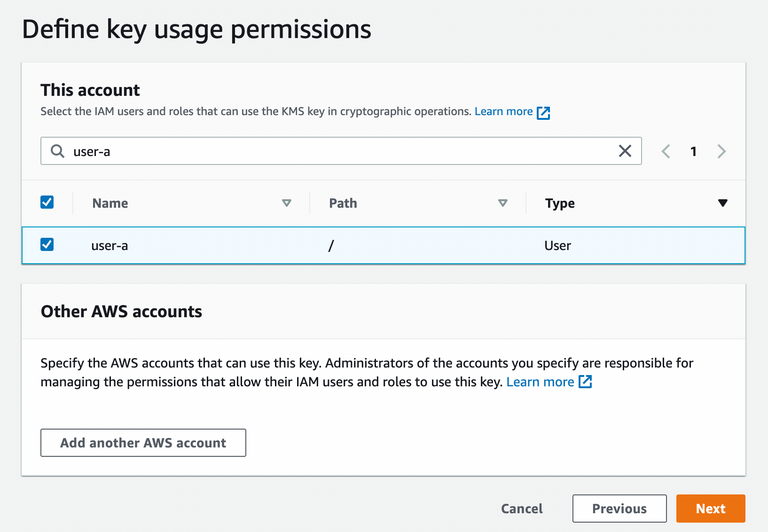
AWS Documentation:
The default key policy that the console creates for KMS keys allows you to choose IAM users and roles in the account and external AWS accounts and make them key users.
Add user-a in Define key usage permissions and hit Finish.
5. Set S3 Bucket with configured KMS
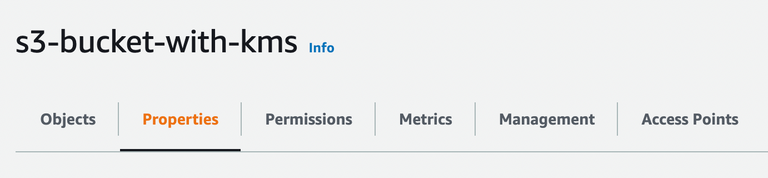
Go to Properties tab. Scroll down to Default Encryption and hit Edit.
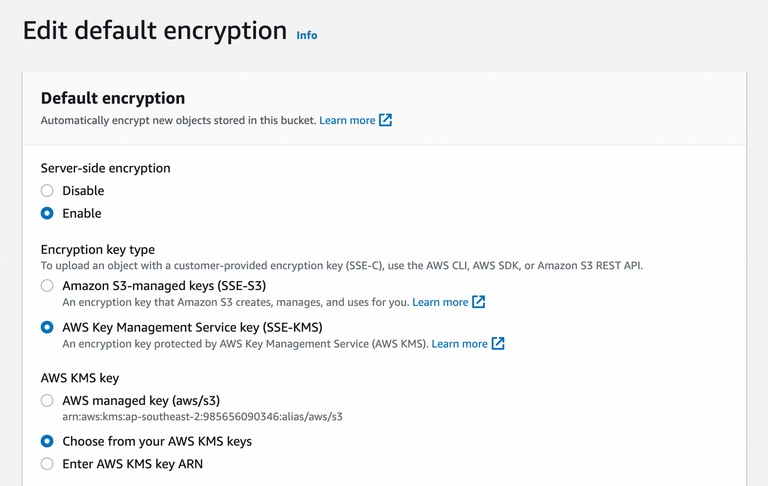
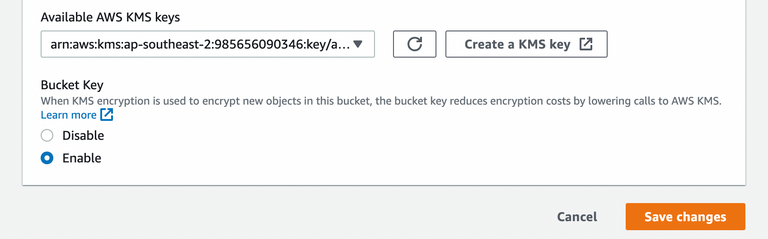
Choose AWS KMS key with configured KMS
6. Try to log out of the current user and log in again with user-a and user-b. You can log in with an incognito browser or another browser to work with.
7. Upload the file to S3 bucket with user-a
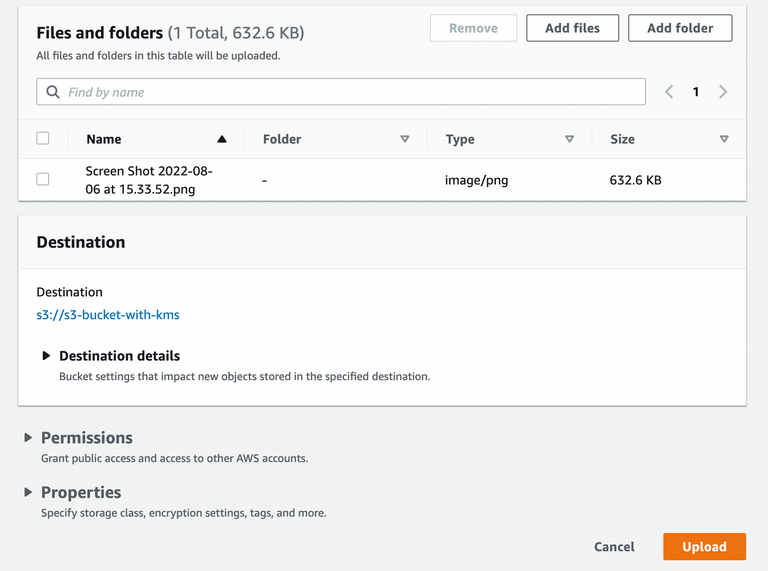
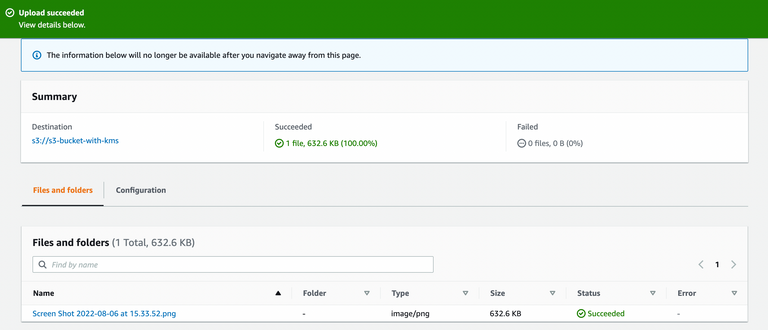
8. Try to log in with user-b and download the file.
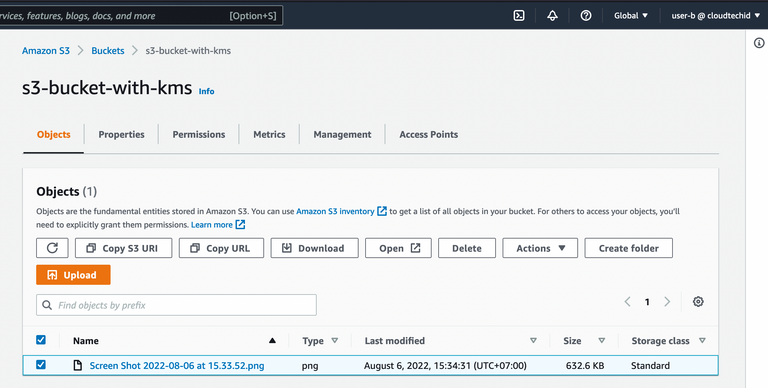
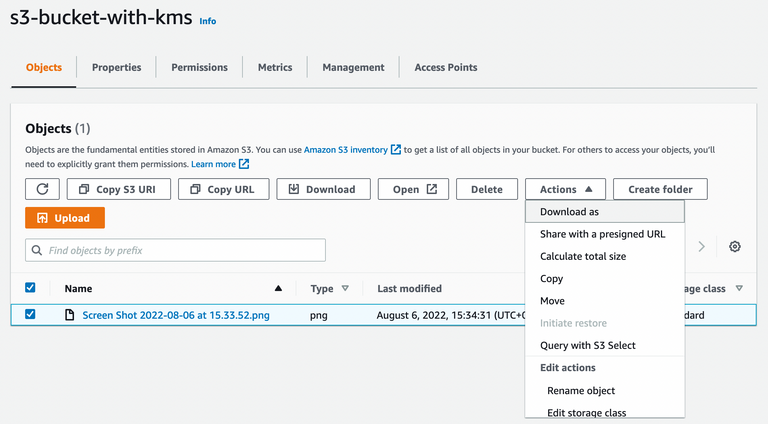
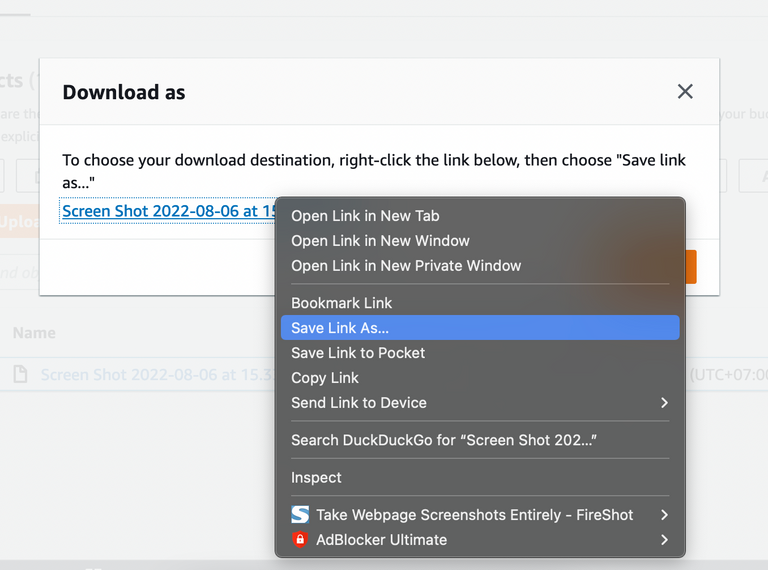
9. Try to open the downloaded file with user-b
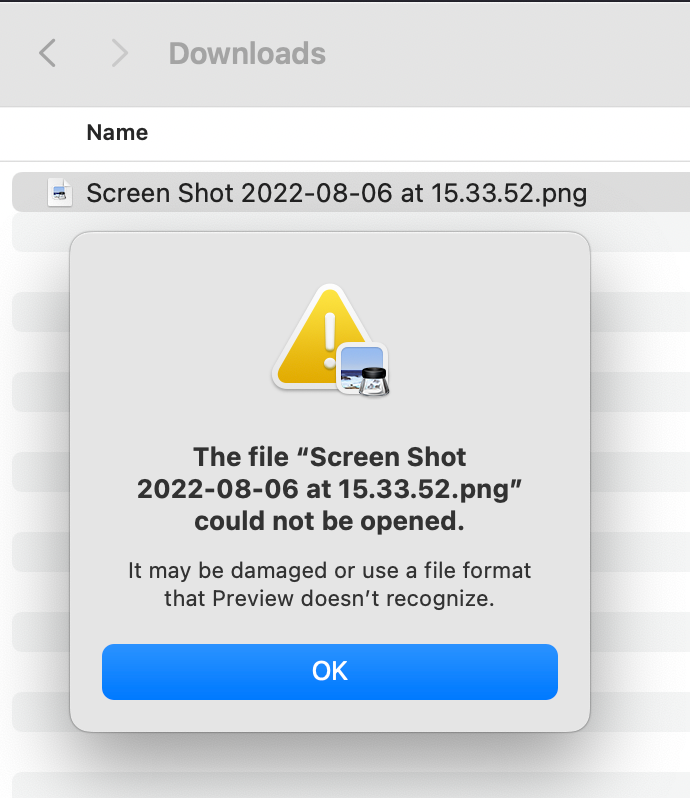
10. Try to download the file and open it with user-a
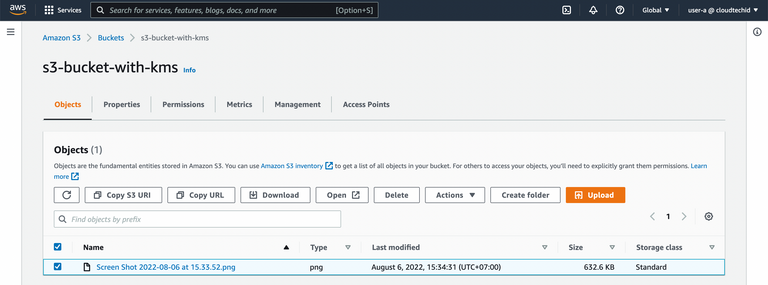
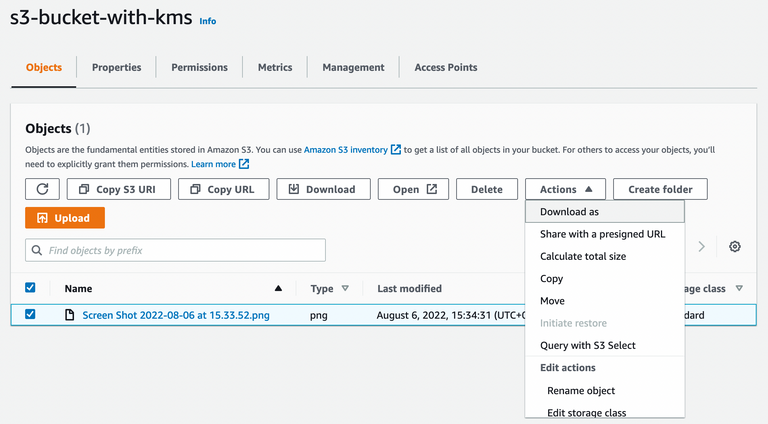
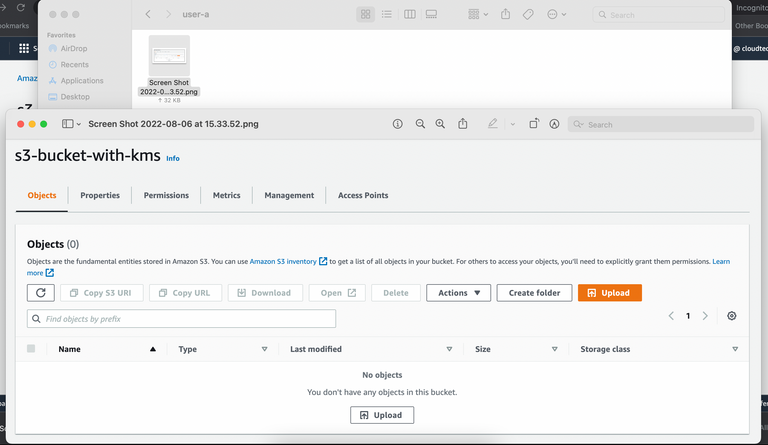
And it works.
That's why using KMS in an S3 bucket is a good idea. You can add permissions to a specific bucket with a policy bucket or add an IAM policy that resides in the user's IAM. Imagine if an intruder got your file and used it carelessly. If hijacking occurs, and the hijacker gets to the file, they won't be able to open it because the file is encrypted with KMS. That way, it's useless for people to get the file if they can't open it.
At Westcon, we have AWS Certified Security Professionals with many years of Security experience at your disposal who can help you analyse and secure your AWS infrastructure using modern, leading-edge tools. If you have any questions or concerns about AWS cloud environment security, please do not hesitate to contact the Partner Success centre (PSC) at
NZ Cloud Sales: +64 9 477 7211 Email: [email protected]
AU Cloud Sales: +61 2 8412 1212 Email: [email protected]
SG Cloud Sales: +65 6424 0570 Email: [email protected]
ID Cloud Sales: +62 21 8062 1470 Email: [email protected]